A Caterham Seven Blog
-

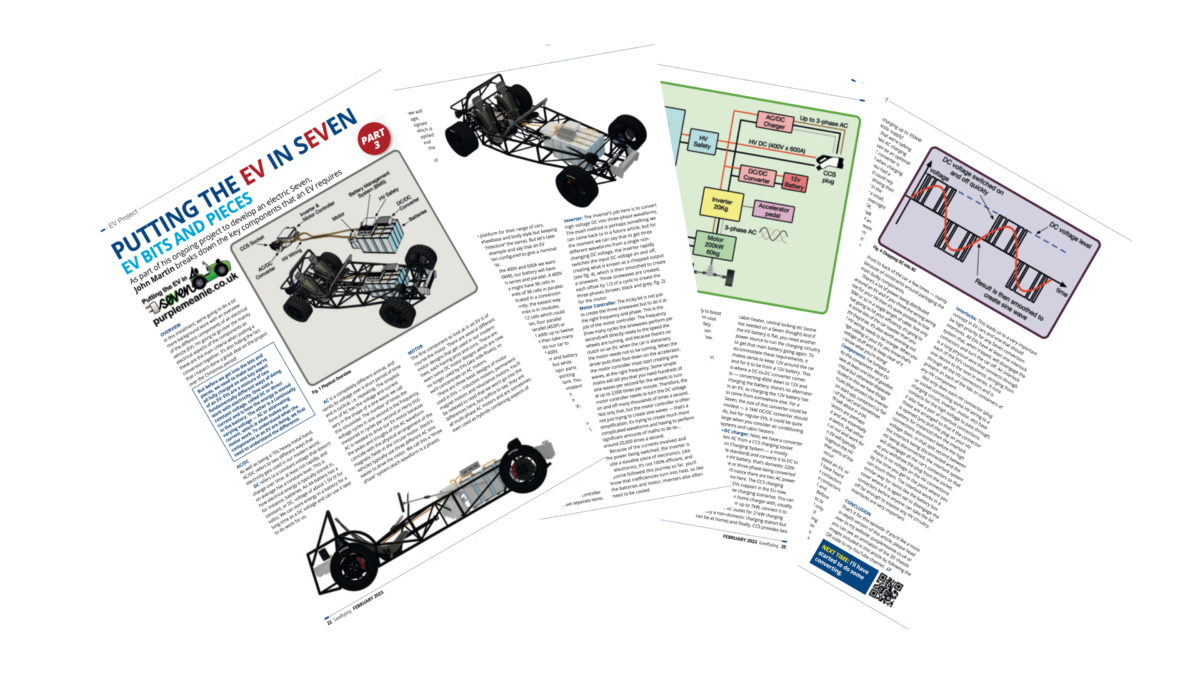
Lowflying December 2022 – Putting the EV in sEVen – Conversion Trade-offs
Another article in Lowflying for December 2022. This is part 2 of a multi-part series and is a cut down version of this post:
-

sEVen Tradoffs and Compromises
A cut down version of this post appeared in the December 2022 edition of Lowflying. This full version is a little more wordy but contains more detail, images and with hyperlinks. Putting the EV in sEVen – Part 2 : Conversion Tradeoffs With my sEVen conversion car now purchased, I’m well and truly getting my feet…
-

It’s not Merchandise
Well I had to, didn’t I? It seemed such a great tag line “Putting the EV in sEVen” that I just had to get some T-shirts printed… and hoodies, polos and fleeces! 🤣 I used a local printing company called Carrillion here in Bristol. They were crazy busy but did manage to get me my stuff…
-

sEVen Conversion – The Victim
Well it’s about time for an update. The victim has been purchased. After searching on and off for a couple of years, not particularly rigorously it must be said, I started looking seriously at the end of the summer (2022) for a “host” car to be the basis for my EV conversion. I’m calling this…
Got any book recommendations?