Category: ECU Diagnostics
-

PTEVIS – Progress #1 youTube Video
Well this video wasn’t quite the mammoth effort that the last two “explainer” videos were, but it still took over 50 hours to make. The video covers the purchase and road registration of the project car from 2022 through to the spring of 2023. I cover the options for getting the car road registered and…
-
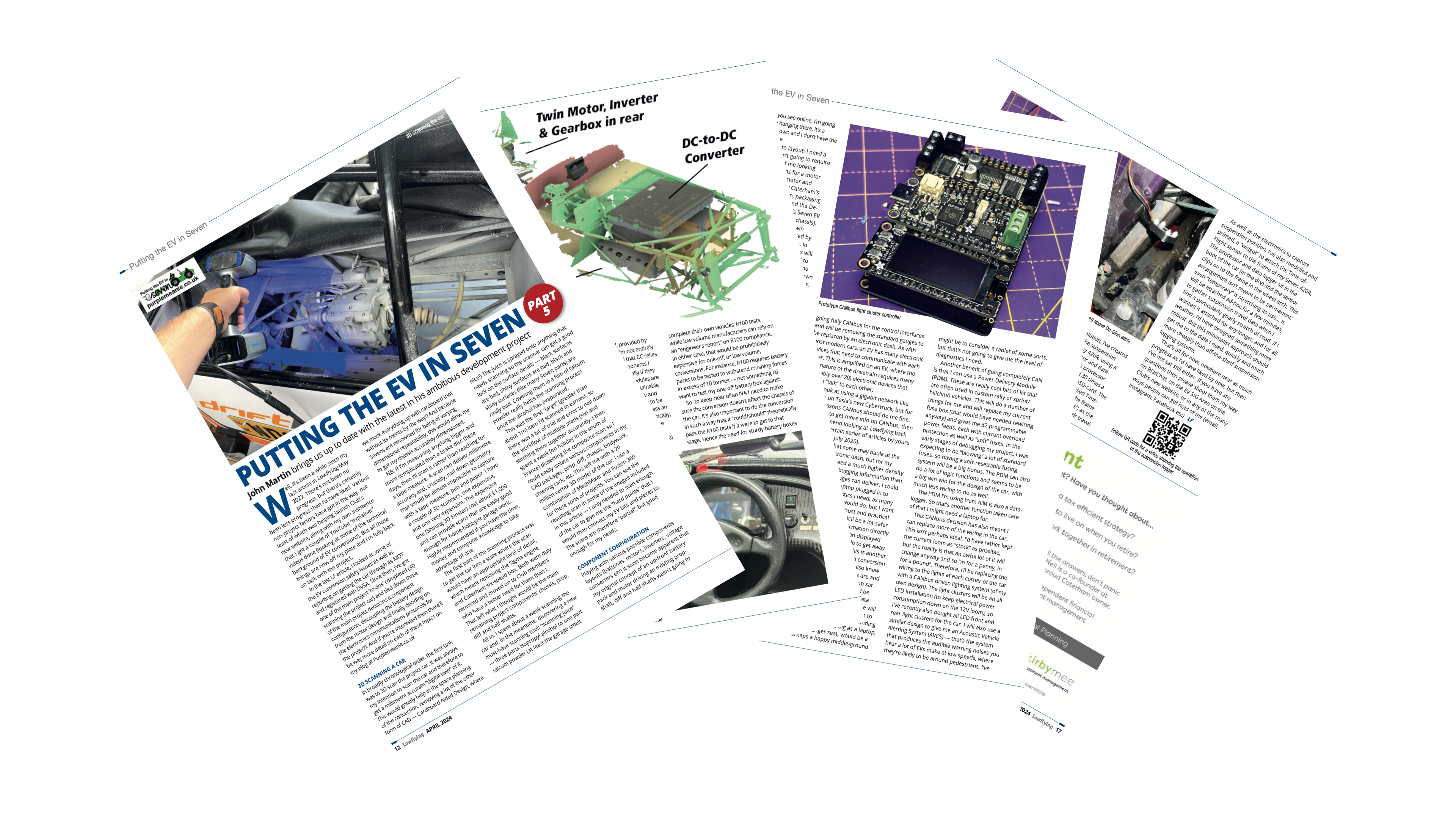
Putting the EV in sEVen – Lowflying part 5 : Spring ’24 Progress
So, it was about time I did an update for the Caterham and Lotus Seven Club magazine, Low Flying. This article is the Spring 2024 progress update and covers: Scanning the Car Component Configuration CANbus Configuration Suspension Logger
-
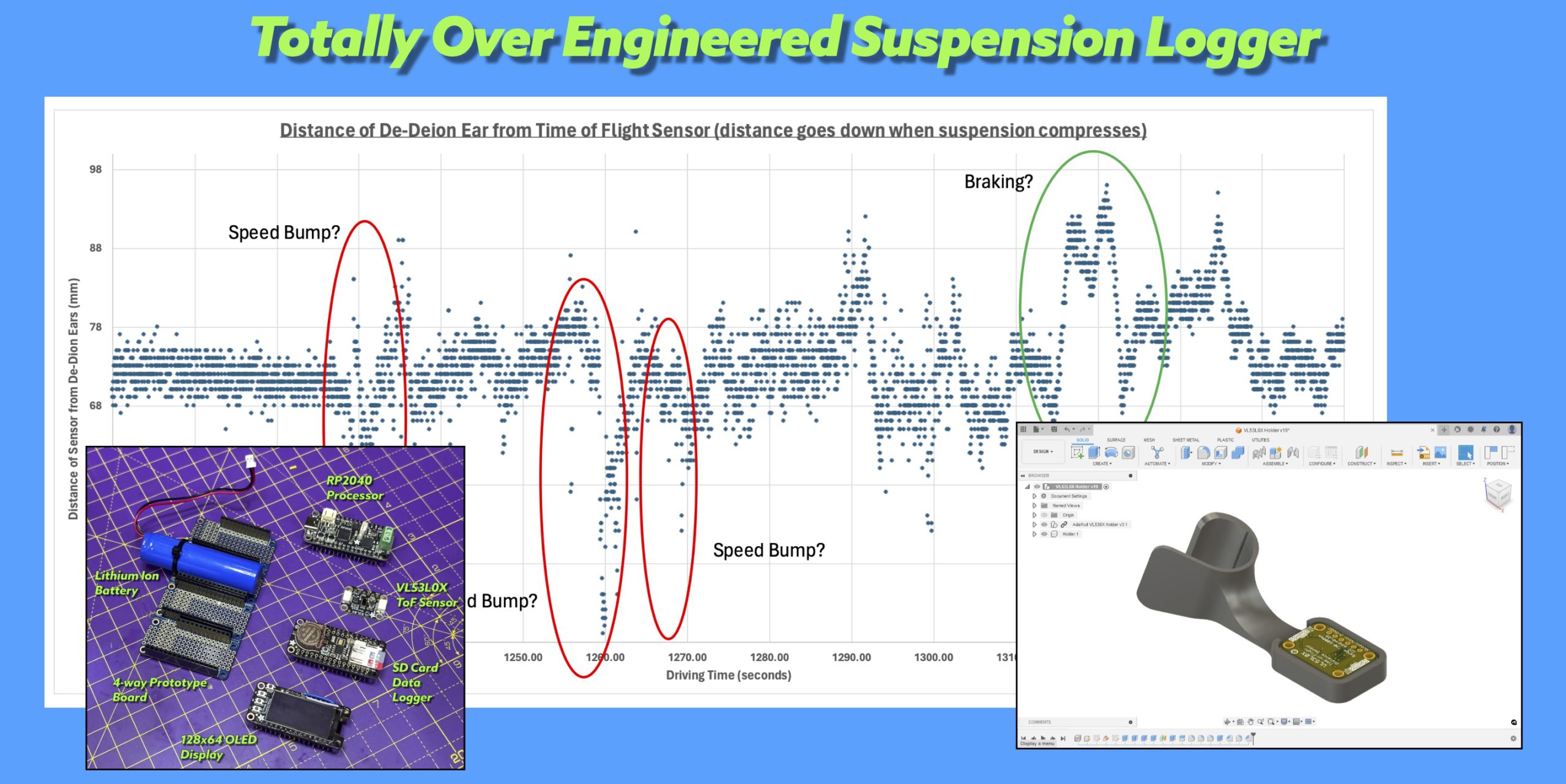
PTEVIS Suspension Logger Mini-Project
As part of my Putting The EV in Seven project, I decided I needed a big detour into suspension travel on a Seven. That sounds like a good route to getting my project finished quickly, right? Well, it goes a bit like this. In a non-linear-timey-wimey sort of way of looking at the PTEVIS project,…
-

ELECTRIC VEHICLE COMPONENTS – YOUTUBE PTEVIS 2.2
This is the second of two explainer videos I’ve created to help YouTube viewers understand the concepts, terminology and physics of what’s going on in my Caterham Seven EV conversion. I’ve made these two videos so I can refer back to them in my progress videos and so I don’t need to explain each concept…
-

The Electric in Electric Vehicles – YOUTUBE PTEVIS 2.1
This is the first of two explainer videos I’ve created to help YouTube viewers understand the concepts, terminology and physics of what’s going on in my Caterham Seven EV conversion. I’ve made the videos so I don’t need to keep explaining each concept every time I mention it in a subsequent video and I’ll be…
-

3D Scanning My EV Conversion Project Car
Excuses, Excuses Ok… so… I’ve been distracted. Since starting this EV conversion project I’ve got a bit distracted by a couple of other projects. The first was the Caterham and Lotus Seven Club, in general and specifically the move to the new website. But I also found I was getting involved in way more other…